BloodHound est un outil permettant de cartographier un environnement Active Directory en le représentant sous forme de graphe. Cette représentation offre alors toute la puissance de la théorie des graphes pour découvrir des chemins d'attaque qui auraient été autrement difficiles voire impossibles à détecter.
Almost every attack on Active Directory you hear about today – no matter if ransomware is involved or not – (ab)uses credential theft techniques as the key..
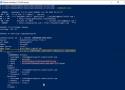
How can pen testers do lateral movement with PSExec? PSExec can provide the ability to easily control of multiple machines on a network.
A real ninja leaves no traces.
Les Failles XSS sont répandues dans les applications web. Principes, types d'attaques, exploitations, nous présentons les XSS et les bonnes pratiques sécurité
Guide to using YubiKey for GPG and SSH. Contribute to drduh/YubiKey-Guide development by creating an account on GitHub.
Introduction Internal networks are rife with lurking threats that often manifest in unexpected ways. Among these, logon scripts, a seemingly innocuous component of user and […]
Explore the Pass-the-Cookie attack, including how adversaries can bypass MFA authentication with it, and learn how to defend against it.
Learn what a primary refresh token (PRT) is and how attackers use the Pass-the-PRT technique to move laterally to a company’s cloud environment.
Les attaques CSRF sont utilisées pour compromettre une application web. Principes, impacts, nous vous détaillons les CSRF et les bonnes pratiques sécurité
Décrit comment configurer la signature SMB et déterminer si la signature SMB est activée.
This blog post focuses on detecting Indicators of Compromise (IoC) for keyloggers that utilize living-off-the-land (LOTL) techniques.
While investigating a different Azure AD vulnerability in December 2022, Secureworks Counter Threat Unit researchers discovered that stored NTHashes could be recovered via the Microsoft Graph API and decrypted using a certificate stored on Azure AD Domain Services (Azure AD DS) domain controllers.
Obfuscation malware
How have you been managing your Docker security without analyzing data? Learn how to enhance your Docker Compose security in this tutorial.
Outil de monitoring des certificats émis via LetsEncrypt.