Un cours de niveau M2 sur l'identité et les méthodes d'authentification
Don’t panic - if you have just exposed a sensitive file or secret to a public git repository, GitGuardian has you covered. Follow our step-by-step guide for best practices to protect your GitHub data from further leaks.
Storing and managing secrets like API keys and other credentials can be challenging. Here are some of the best practices to help keep secrets and credentials safe.
Cet article évoque les menaces liées à l'utilisation de l'IPv6 sur Windows, ainsi que les méthodes de protection clés en main contre les vulnérabilités IPv6.
User manual, installation and configuration guides. Learn how to get the most out of the Wazuh platform.
By default, all communication between a MySQL or MariaDB server and its clients is unencrypted. That’s fine if both the database server and client are on the same machine, or connected by a network you fully control, but as soon as anything touches the internet — or even an internal data center network the NSA may have secretly tapped into — all bets are off, and you need SSL to ensure that the communication cannot be spied on or tampered with. This post will guide you through the entire process in an abundance of detail.
Active Directory and Internal Pentest Cheatsheets
Sécuriser les flux échangés entre les clients et les serveurs DNS est possible grâce à TSIG et DNSSEC, afin d'éviter qu'ils circulent en clair sur le réseau.
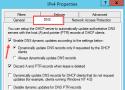
In this post, we're going to learn to Configure DNS Dynamic Update in Windows DHCP Server and prevent issues with client name resolution.
Je vois sur Internet des serveurs Proxmox pas sécurisés voire pire, des conseils qui préconisent d’u...
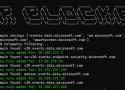
In this blog, we will see the process of how to detect the credential access attacks on Linux endpoints using Wazuh. Credential access attacks target various sensitive information like browser data, password managers, SSH keys, and hashed passwords.
Information Security Services. Offensive Security, Penetration Testing, Mobile and Application, Purple Team, Red Team
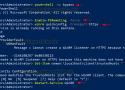
Installation du module GPG sur Powershell.
Chiffrement symétrique avec GPG.
Easy and secure password rotation for Linux and Windows system accounts - scarolan/painless-password-rotation
Windows Remote Management (WinRM) is a protocol developed by Microsoft for remotely managing hardware and operating systems on Windows machines. It is a component of
Blog with insights about information security from the perspective of a team of penetration testers.
The latest version of the whistleblowing platform SecureDrop runs on the Qubes operating system. At the Guardian we used the Salt management engine to set up a Qubes environment where journalists could safely interrogate sensitive documents.
Automated Linux evil maid attack. Contribute to AonCyberLabs/EvilAbigail development by creating an account on GitHub.