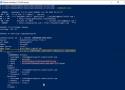
MTLS with Traefik & Smallstep
How do I mount /tmp with nodev, nosuid, and noexec options to increase the security of my Linux based web server? How can I add nodev, nosuid, and noexec options to /dev/shm under Linux operating systems?
The noexec option in /etc/fstab (File System Table) in Linux is a mount option that specifies how a filesystem should be mounted, particularly with regard to the execution of binaries. When a partition is mounted with the noexec option, it means that you cannot execute any binaries that are stored on that partition. Understanding /etc/fstab …
Wormhole vous permet de partager des fichiers avec un chiffrement de bout-en-bout et un lien qui expire automatiquement.
wtf-form
Les attaques CSRF sont utilisées pour compromettre une application web. Principes, impacts, nous vous détaillons les CSRF et les bonnes pratiques sécurité
Décrit comment configurer la signature SMB et déterminer si la signature SMB est activée.
This blog post focuses on detecting Indicators of Compromise (IoC) for keyloggers that utilize living-off-the-land (LOTL) techniques.
The following is a new how-to guide for users who are starting out with Qubes OS. You can also find it in our documentation under How to organize your qubes. When people first learn about Qubes OS, their initial reaction is often, “Wow, this looks really cool! But… what can I actually d...
Dans cet article, je vais vous présenter quelques méthodes pour tracer les accès et tentatives d'accès d'un programme sur les fichiers d'un système Linux.
While investigating a different Azure AD vulnerability in December 2022, Secureworks Counter Threat Unit researchers discovered that stored NTHashes could be recovered via the Microsoft Graph API and decrypted using a certificate stored on Azure AD Domain Services (Azure AD DS) domain controllers.
Learn how to detect successful SSH brute force attacks and other advanced behaviors using the conditional bucket feature in CrowdSec Security Engine 1.5.
Containers are no virtual machines - yet we might want to treat hosts running container workloads like hypervisors and apply limitations on container networking. This guide describes a way to limit container networking on docker based container hosts using firewalld.
An easy to use editor for crontab schedules.