This article provides general guidance for securing SQL Server running in an Azure virtual machine.
MySQL and MariaDB are relational databases used in many unique situations. However, they can pose a security risk for your system and your data if you do no…
Learn how to secure your PostgreSQL database. Guide for PostgreSQL security hardening best practices. Get tips about securing PostgreSQL encryption, authentication, access, roles, and many more.
In this tutorial, we will show an essential first step toward mitigating the specific risk that can be created when configuring PostgreSQL to allow remote co…
Dans cet article, Dor Segal, chercheur principal en sécurité, vous présentera ses recherches pour découvrir comment utiliser les attaques MITM pour contourner FIDO2.
Have you heard about SOPS? If you have already been in a situation where you needed to share sensitive information with your teammates, this is for you.
Secrets management in Docker is a critical security concern for any business. When using Docker containers, it is essential to keep sensitive data such as passwords, API keys, and other credentials secure.
Snaffler va permettre de rechercher les informations sensibles dans les partages de fichiers présents sur les serveurs, en environnement Active Directory.
Comment sauvegarder et restaurer une GPO ou toutes les GPO de son domaine Active Directory ? La réponse dans notre cours sur les stratégies de groupe.
Il existe deux manières d'exporter et d'importer des objets de stratégie de groupe : vous pouvez utiliser la console de gestion des stratégies de groupe (GPMC) ou vous pouvez utiliser PowerShell. Sauvegarder, Exporter, Crée & Importer des GPO en PowerShell n'aura plus de secret pour vous
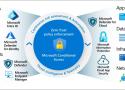
Conditional Access Policies - In Depth Guide
La méthode Trim() de PowerShell permet d'éliminer les espaces inutiles ou les caractères inutiles, en début et fin de chaîne. Voici des exemples d'utilisation.
This week the House is set to vote on legislation to renew Section 702 of the Foreign Intelligence Surveillance Act (“FISA 702”), along with a set of amendments. One of these amendments — put forward by House Intelligence Committee leads Mike Turner and Jim Himes — would expand warrantless FISA surveillance dramatically: While falsely billing […]
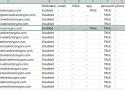
In this guide, you will learn how to get the MFA status of Office 365 users with PowerShell. I’ll show you how to get MFA status for a single and a list of…
Accumulation de couches de sécurité imparfaites mais améliorant le niveau de sécurité au final.
We needed a quick way to fix containers without having to rebuild everything. When security issues in container images pop up and bad guys might exploit them soon after they’re known, we really have…
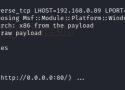
Introduction Indirect Command Execution is a defense evasion technique that is often used by Red Teams in which an adversary tries to bypass certain defense
Posts about conhost written by Administrator